Recent News
- Dr Aswani on Blockchain-Based Self-Sovereign Identity Management August 31, 2025
 The book chapter “A Novel Blockchain-Based Self-Sovereign Identity Management System for IoT Devices” is a transformative exploration within the book “Decentralized Identity Systems: Innovations and Challenges.” Authored by Dr Aswani Devi Aguru, Assistant Professor, Department of CSEand co-authored by Dr Suresh Babu Erukala NIT Warangal, this chapter delves into the critical intersection of blockchain technology and identity management, specifically tailored for the rapidly evolving Internet of Things (IoT) landscape.
The book chapter “A Novel Blockchain-Based Self-Sovereign Identity Management System for IoT Devices” is a transformative exploration within the book “Decentralized Identity Systems: Innovations and Challenges.” Authored by Dr Aswani Devi Aguru, Assistant Professor, Department of CSEand co-authored by Dr Suresh Babu Erukala NIT Warangal, this chapter delves into the critical intersection of blockchain technology and identity management, specifically tailored for the rapidly evolving Internet of Things (IoT) landscape.Brief Introduction of the Book Chapter.
This book chapter presents a novel blockchain-based self-sovereign identity (SSI) management system that promotes global interoperability by generating decentralized, secure, and unique identifiers for edge devices worldwide. The proposed system leverages the power of permissioned Blockchain, specifically Hyperledger Indy, a distributed ledger technology (DLT) designed for creating and managing decentralized identities. The EdDSA-based key management and Plenum Byzantine Fault Tolerant (BFT)-based consensus algorithm introduce novelty and effectiveness in the proposed framework compared to state-of-the-art works on identity management. The performance of Hyperledger Indy Blockchain is tested on Hyperledger Caliper in terms of run time of operations and transaction throughput. We proclaim that our work is one of the earliest studies on Blockchain-based SSI management on Hyperledger Indy.
Significance of the Book Chapter
The author expresses strong enthusiasm for designing novel frameworks for IoT device authentication utilising ECC and AEAD primitives, in addition to developing identity management solutions based on SSI. The alignment of the book’s topics with current research highlights their significance in the progression of these critical areas.
Target Audience:
Very limited research has been carried out on SSI for IoT devices. Researchers will find the book chapter helpful in beginning their research on Blockchain-based decentralised identity management of IoT devices.
Co-authors or other Major Contributors
Dr Suresh Babu Erukala is a co-author. He is working as an Associate Professor in the Department of CSE at NIT Warangal.
- A Secure Framework for Embedding Secret Messages within Cover Images August 31, 2025
 The Department of Computer Science and Engineering has filed and published a patent application titled “System and Method for Securely Concealing a Secret Message within a Cover Image” (Application No. 202541072940) in the Patent Office Journal. The invention is credited to Dr Subhankar Ghatak, Assistant Professor, Department of CSE, Dr Aurobindo Behera, Lecturer, Department of CSE (SRM Education), Ms Sharifa Jahan Shaik, U G Student, Department of CSE, and Ms Vasigani Jhansy Archana, Ph.D. Student, Department of CSE.
The Department of Computer Science and Engineering has filed and published a patent application titled “System and Method for Securely Concealing a Secret Message within a Cover Image” (Application No. 202541072940) in the Patent Office Journal. The invention is credited to Dr Subhankar Ghatak, Assistant Professor, Department of CSE, Dr Aurobindo Behera, Lecturer, Department of CSE (SRM Education), Ms Sharifa Jahan Shaik, U G Student, Department of CSE, and Ms Vasigani Jhansy Archana, Ph.D. Student, Department of CSE.This innovation introduces a new paradigm in data hiding, advancing beyond conventional steganography techniques. Unlike traditional methods that subtly alter a cover image to embed secret information, this approach leaves the image entirely untouched.
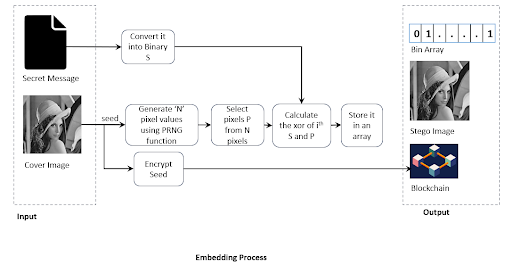
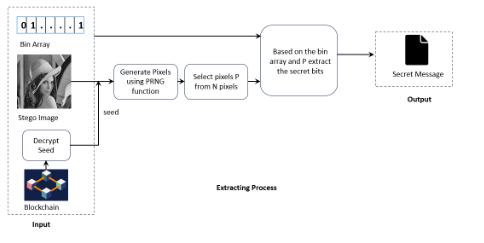
By leveraging Pseudo-Random Number Generation (PRNG) in combination with the cover image and securely storing the PRNG seed value on the Blockchain, the system achieves unparalleled data security and integrity. As a result, the cover image remains completely unmodified, ensuring minimal distortion and highly reliable message retrieval.
Abstract :
This invention presents a novel approach to data hiding that differs from conventional steganography techniques. Unlike traditional methods, which modify the cover image to embed secret data, this methodology ensures the cover image remains completely unaltered. The technique employs Pseudo-Random Number Generation (PRNG) in conjunction with an array and the cover image to conceal secret data. The PRNG seed value is securely stored on the Blockchain, thereby enhancing both uniqueness and security. Since the cover image undergoes no modification, the proposed approach achieves a minimal Mean Squared Error (MSE) for the extracted secret image.To hide a message in a picture, the usual way is to change the picture slightly—for example, by altering a few pixels so the difference is hard to notice. But if someone examines the image very closely, they might detect something unusual. Our method works differently. It’s like hiding a treasure without ever touching the map. Instead of altering it, we use a secret formula and a random number generator to decide where the hidden information would be if we needed to retrieve it later. The key to that formula is securely stored on the Blockchain, like locking it inside an unbreakable safe. As a result, the picture stays 100% original with no changes, and only the person who has the Blockchain secret key can uncover the hidden message.
Practical implementations :
Military Communication: Steganography can securely encode sensitive data, like that of meeting locations (latitude and longitude), ensuring that critical information remains hidden from adversaries.
Password Protection: Individuals can embed passwords within images, offering an additional layer of security and reducing the risk the unauthorized access.
Covert Communication: Activists or journalists in repressive regimes can use steganography to communicate securely by hiding messages within innocuous-looking images or files.
Medical Image Security: In healthcare, patient data can be securely embedded within medical images, ensuring data confidentiality while sharing the images with specialists.Future research plans:
AI-Assisted Stealth Optimisation: Use Machine Learning to predict detection patterns and further improve the undetectability of hidden data.
Cross-Platform Media Support: Extend beyond images to videos, audio streams, and 3D models, ensuring zero modification across formats.
Continue reading →