Security concerns in digital image transmission over the internet
 The research team from the Department of Computer Science and Engineering proposes a research scheme to address security concerns in the transmission of digital images of aerial Remote sensing images over the Internet. Assistant Professor Dr Priyanka, Assistant Professor Dr Jatindra Kumar Dash, research scholar Ms K Jyothsna Devi, and BTech student Mr. M V Jayanth Krishna, published the paper A New Robust and Secure 3-Level Digital Image Watermarking Based on G-BAT Hybrid Optimization in the Mathematics Journal SCI, a Q1 Journal with an Impact Factor of 2.9. The research project combats various threats in the transmission of Remote sensing images, such as copyright protection, copy control, and unauthorized access.
The research team from the Department of Computer Science and Engineering proposes a research scheme to address security concerns in the transmission of digital images of aerial Remote sensing images over the Internet. Assistant Professor Dr Priyanka, Assistant Professor Dr Jatindra Kumar Dash, research scholar Ms K Jyothsna Devi, and BTech student Mr. M V Jayanth Krishna, published the paper A New Robust and Secure 3-Level Digital Image Watermarking Based on G-BAT Hybrid Optimization in the Mathematics Journal SCI, a Q1 Journal with an Impact Factor of 2.9. The research project combats various threats in the transmission of Remote sensing images, such as copyright protection, copy control, and unauthorized access.
Abstract
This contribution applies tools from the information theory and soft computing (SC) paradigms to the embedding and extraction of watermarks in aerial remote sensing (RS) images to protect copyright. By the time 5G came along, Internet usage had already grown exponentially. Regarding copyright protection, the most important responsibility of the digital image watermarking (DIW) approach is to provide authentication and security for digital content. The main goal of the paper is to provide authentication and security to aerial RS images transmitted over the Internet by the proposal of a hybrid approach using both the redundant discrete wavelet transform (RDWT) and the singular value decomposition (SVD) schemes for DIW. Specifically, SC is adopted in this work for the numerical optimisation of critical parameters. Moreover, 1-level RDWT and SVD are applied to digital cover images and singular matrices of LH and HL sub-bands are selected for watermark embedding. Further selected singular matrices S LH and S HL are split into 3 × 3 non-overlapping blocks, and diagonal positions are used for watermark embedding. Three-level symmetric encryption with a low computational cost is used to ensure higher watermark security. A hybrid grasshopper–BAT (G- BAT) SC-based optimization algorithm is also proposed to achieve high-quality DIW outcomes, and a broad comparison against other methods in the state-of-the-art is provided. The experimental results have demonstrated that the proposal provides high levels of imperceptibility, robustness, embedding capacity, and security when dealing with DIW of aerial RS images, even higher than the state-of-the-art methods.
The proposed scheme is easily dumped into the sender and receiver machines to work readily. MATLAB platform is the only requirement. Researchers aspire to design new image watermarking schemes using machine learning and deep learning techniques. For this project, they have collaborated with Professor José Santamaría from the Department of Computer Science, University of Jaén, and Professor Antonio Romero-Manchado from the Department of Cartographic Engineering, Geodesy, and Photogrammetry, University of Jaén.
- Published in CSE NEWS, Departmental News, News, Research News
Dr Saleti Sumalatha published two patents in a row

The Department of Computer Science and Engineering is glad to announce that Assistant Professor Dr Saleti Sumalatha and her students got two of their patent applications published in a row. The patent titled “System and method for mining of constraint based high utility time interval sequential patterns” (Application number: 202241044001) was published in collaboration with the BTech students; K Rasagna, N Naga Sahithya, K Hemalatha, B Sai Charan, and Upendra Karthik.
The main intention of the proposed system is to discover the sequences that include the time period between the purchases of each item. For example, if we consider a shop which sells some groceries like Grains, Milk, Yogurt, Bread and Eggs as the set of items in the database. Now, the main aim is to find the time period between the purchases of particular items that are being sold. From this, the shop owner can easily maintain the stock of completed items according to the time period.
For example, an output sequential pattern including time intervals of the form indicates that a customer who purchased item x also bought item y after three months and visited the store again after five months to buy item z. It considers the same utility threshold for each of the items in the database, which shows that each item is assumed to have the same unit profit. This is not convincing as each item is different in real-time applications and should not be treated equally. For example, the sales of” Gold bangles” will produce more profit than the sales of” Cotton Jeans”. In view of this, the research proposes UIPrefixSpan-MMU.

The other patent titled “A system and a method for automatic essay grading” (Application number: 202241043045) was published in collaboration with M Purnima, G Haveela, K U Meghana, and S Deepthi Reddy. Essay grading systems are being adopted by different organisations to reduce the hectic workload from a teacher’s point of view. They made a model which is trained with datasets containing different essay topics and numerous essays with scores varying in a wide range.
Essay grading systems will not only save the time for evaluation but also give accurate results. The output of the system will be quick such that it could evaluate many essays and get trained. This system benefits both the student and the teacher as well. Their model predicts the scores of the essay by comparing them with the features extracted from the trained data. This model can be used to reduce the effort of teachers to grade many essays in a limited time. The work of grading will be fastened and accurate.
- Published in CSE NEWS, Departmental News, News, Research News
Applications of federated learning in computing technologies

The Department of Computer Science and Engineering is delighted to announce that Assistant Professors, Dr Sambit Kumar Mishra and Dr Tapas Kumar Mishra, and the final year BTech students – Kotipalli Sindhu, Mogaparthi Surya Teja, Vutukuri Akhil, Ravella Hari Krishna, and Pakalapati Praveen – published a chapter titled Applications of Federated Learning in Computing Technologies in the scopus-indexed book titled Convergence of Cloud with AI for Big Data Analytics: Foundations and Innovation, a Wiley publication.
The book chapter describes the application of federated learning to various computing technologies. The federated learning concept is similar to the client-server model, where the client sends data to the server for processing and the processed data is again sent to the client. But, in federated learning, the clients are allowed separately to teach the deep neural network models with the local data combined with the deep neural network model at the central server.
Federated learning is a machine learning technique that trains the knowledge across different decentralized devices holding samples of information without exchanging them. The concept is additionally called collaborative learning. Researchers have used large frameworks for all the computations in the past years, and then they have moved to client-server frameworks.
It is also like a traditional centralised machine learning technique. All the local datasets are uploaded to a minimum of one server, so it assumes that local data samples are identically distributed. Because of its security and privacy concerns, it’s widely utilised in many applications like IoT, cloud computing; Edge computing, Vehicular edge computing, and many more. In the chapter, different applications of federated learning, their privacy concerns, and their definition in various fields of computing technologies like IoT, Edge Computing, Cloud Computing, Vehicular edge computing, etc. are presented. It will be of advantage to graduate students, researchers, academicians, institutions, and professionals that are interested in exploring the areas of intelligent computing systems.
- Published in CSE NEWS, Departmental News, News, Research News
An incredible journey to the India Book of Records

It is a moment of immense pride for SRM University- AP to welcome a new record maker into our midst. P Vishnu Vardhan from the Department of Computer Science Engineering has carved his name into the India Book of Records for performing 48 double-under jump rope skips in 20 seconds. He has also managed to set two records in the National Book of World Records. When most surrender their favourite hobbies to the rush of our work and academic life, this incredible student has displayed hardwork and dedication to transform his hobby into a national record.
Mr Vishnu Vardhan comments on the multiple times he succumbed to giving up his hobby of skipping ropes but realised that it was a space of refuge amidst the pressures of the world. He has shown an incredible feat of courage and dedication to set this impressive record by braving the rejection that he initially had faced.
“When I came to know about the India Book of Records, it was my parents who made me apply for it but I was rejected the first time. I had lost all hope but my friends supported me to pursue my passion for skipping rope and also helped with my academics. Finally I have entered into the National Book of Records, twice and the India Book of Records as well”, he said.
He has extended a heartfelt note towards his parents and his friends, M Surya Teja and K Nithin, for their undying support and confidence that has guided him to attain this amazing achievement.
Mr Vishnu Vardhan hopes to represent SRM University- AP at the All India Inter University rope skipping competition and provide further laurels for the institution. His journey to setting national records proves that with passion, endurance and a generous amount of optimism, even the unachievable could be achieved.
- Published in CSE NEWS, Departmental News, News, Sports News, Students Achievements
15 Lakh investment for Manideep’s Hatchlab venture SPOCSQ Pvt
 Making an impact on society through revolutionary innovations is not an everyday thing. Manideep Surusomayajula from the Department of Computer Science and Engineering bagged an investment of 15 Lakh for his Hatchlab venture SPOCSQ Pvt. This is the first investment that has been secured by the startup project.
Making an impact on society through revolutionary innovations is not an everyday thing. Manideep Surusomayajula from the Department of Computer Science and Engineering bagged an investment of 15 Lakh for his Hatchlab venture SPOCSQ Pvt. This is the first investment that has been secured by the startup project.
His startup deals with chip-based certification processes using Blockchain Technology. SPOCSQ is in the process of developing a tamper-proof certificate system based on chip and blockchain technology.
The investing company ThredzIT Information Technology Pvt. Ltd is willing to invest 20-30 Lakh for the final version of the product. This achievement is a milestone in Manideep’s career as it demonstrates his passion for entrepreneurship and innovation.
- Published in CSE NEWS, Departmental News, IDEA NEWS, News, Students Achievements
A champion in the making!

Mastering martial arts is not an easy feat as it demands an exorbitant amount of effort from our physical as well as mental capability. Truly excelling in a martial art form can only be achieved through the manifestation of hardwork, perseverance and unwavering willpower. The Department of Computer Science and Engineering is proud to announce that Ms Bala Ramya Sri Yerramreddy has been selected for the Wushu Championship at the 36th National Games, 2022.
Ms Bala Ramya had previously secured gold at both District and State Level Wushu competitions. Through her journey, she has exhibited strong willpower and dedication to reach these heights. She encourages students to pursue any field of sports or martial arts to attain a peaceful mental constitution as well as physical well-being. Martial arts also equips one with self-defence techniques against physical conflict.
Wushu, an ancient form of hard and soft Chinese martial arts, trains students with superior combat skills for self-defence and promotes sound mental and physical health. One is truly robust only with a healthy balance between well-tuned mind and body.
Her journey to the National Games 2022 representing the state of Andhra Pradesh is awe inspiring and an accomplishment of incredible pride.
- Published in CSE NEWS, Departmental News, News, Sports News, Students Achievements
Youth empowerment and skill development programme concluded

The Department of Computer Science and Engineering at SRM University-AP commenced a one-month-long programme on “Youth Empowerment and Skill Development”. The programme, organised under the ISR activities of the university, was an exclusive initiative for young people living in vicinal rural communities. The sessions aimed to enhance and develop their technical and computing skills to augment their possibilities for a better livelihood.
90 youths were given training on programmes and applications like Microsoft office and Frontend Tools for Web Development. The programme received an overwhelming response from around fifteen neighbouring villages. The young community from the villages; Mangalagiri, Pedavadlapudi, Kaza, Neerukonda, Lemalle, Navuluru, Kuragallu, Velagapudi, Nekkallu, Chiraravuru, Kanteru, Pedaparimi, Yerrabalem, Mandadam, and Sibiram; participated in the training programme.
Assistant Professors of the Department of Computer Science and Engineering, Dr Dinesh Reddy and Dr Mahesh Kumar, were the chief resource persons for the programme. Classes were held from August 29, 2022, to September 28, 2022, at the university premises. The valedictory function was conducted on October 13, and certificates were issued to the participants who had successfully completed the programme. Prof Manoj K Arora, Vice-Chancellor and Prof T Ragunathan, Associate Dean-in-Charge (Engineering) – School of Engineering and Sciences, were also present on the occasion.
- Published in CSE NEWS, Departmental News, News
AKAP-IoV: Facilitating an intelligent transportation infrastructure
 Intelligent transport systems embedded with latest technology is the future of automotive industry and can revolutionise the very infrastructure and architecture of transportation. The principles of intelligent transportation systems have manifested in the development of Internet of vehicles (IoV), a novel technological network that enables autonomous and connected mobile commutation facility. Dr Sriramulu Bojjagani, Assistant Professor, Department of Computer Science and Engineering, has published a paper on this seminal topic titled “Secure Authentication and Key Management Protocol for Deployment of Internet of Vehicles (IoV) Concerning Intelligent Transport Systems” in the prestigious journal, IEEE Transactions on Intelligent Transport Systems (Q1 journal) having an Impact factor of 9.551. The paper highlights the development and significance of the pioneering AKAP-IoV system in successfully tackling cyber threats and security vulnerabilities.
Intelligent transport systems embedded with latest technology is the future of automotive industry and can revolutionise the very infrastructure and architecture of transportation. The principles of intelligent transportation systems have manifested in the development of Internet of vehicles (IoV), a novel technological network that enables autonomous and connected mobile commutation facility. Dr Sriramulu Bojjagani, Assistant Professor, Department of Computer Science and Engineering, has published a paper on this seminal topic titled “Secure Authentication and Key Management Protocol for Deployment of Internet of Vehicles (IoV) Concerning Intelligent Transport Systems” in the prestigious journal, IEEE Transactions on Intelligent Transport Systems (Q1 journal) having an Impact factor of 9.551. The paper highlights the development and significance of the pioneering AKAP-IoV system in successfully tackling cyber threats and security vulnerabilities.
Abstract
Intelligent transport systems amalgamated with advanced technologies are an important element of the automotive industry, including critical infrastructure and transportation. Internet of Vehicles (IoV) is the modern technological framework designed for intelligent transportation. IoV creates a network of information relations among vehicles, thus contributing to reduced congestion, roadside infrastructure, driver/traveller safety, and traffic efficiency through wireless communication and sensing technology. However, a significant challenge in IoV applications is security, as criminals could potentially exploit these applications. Despite increasing industry awareness, the potential danger posed by security vulnerabilities and cyber threats remains high. In this study, we have designed a new system called AKAP-IoV, which supports secure communication, mutual authentication, and key management among vehicles, roadside units, and fog and cloud servers. AKAP-IoV was tested and verified using Scyther and Tamarin to ensure its resistance to cyber threats. Furthermore, we conducted a formal security analysis using the Real-or-Random (RoR) oracle model to assess security properties logically. In addition, a detailed, comprehensive comparative study was considered to evaluate the performance, functionality, efficiency, and security features supported by AKAP-IoV compared to those of recently developed schemes.
- Published in CSE NEWS, Departmental News, News, Research News
Exploring the Potential of an Image Description Generator
An Image caption generator system implies the detection of the image as well as producing the caption with natural language processing by the computer. This is a tedious job. Image caption generator systems can solve various problems, such as self-driving cars, aiding the blind, etc.
The recent research at the Department of Computer Science and Engineering proposes a model to generate the captions for an image using ResNet and Long Short-Term Memory. Assistant Professors Dr Morampudi Mahesh Kumar and Dr V Dinesh Reddy have published the paper Image Description Generator using Residual Neural Network and Long-Short-Term Memory in the Computer Science Journal of Moldova with an impact factor of 0.43.
The captions or descriptions for an image are generated from an inverse dictionary formed during the model’s training. Automatic image description generation is helpful in various fields like picture cataloguing, blind persons, social media, and various natural language processing applications.
Despite the numerous enhancements in image description generators, there is always a scope for development. Taking advantage of the larger unsupervised data or weakly supervised methods is a challenge to explore in this area, and this is already there among the future plan of the researchers. Another major challenge could be generating summaries or descriptions for short videos. This research work can also be extended to other sets of natural languages apart from English.
Abstract
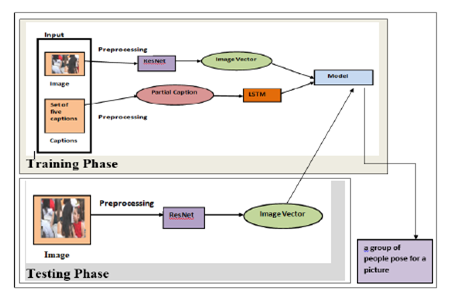 Human beings can describe scenarios and objects in a picture through vision easily, whereas performing the same task with a computer is a complicated one. Generating captions for the objects of an image helps everyone to understand the scenario of the image in a better way. Instinctively describing the content of an image requires the apprehension of computer vision as well as natural language processing. This task has gained huge popularity in the field of technology, and there is a lot of research work being carried out. Recent works have been successful in identifying objects in the image but are facing many challenges in generating captions to the given image accurately by understanding the scenario. To address this challenge, we propose a model to generate the caption for an image. Residual Neural Network (ResNet) is used to extract the features from an image. These features are converted into a vector of size 2048. The caption generation for the image is obtained with Long Short-Term Memory (LSTM). The proposed model was experimented with on the Flickr8K dataset and obtained an accuracy of 88.4%. The experimental results indicate that our model produces appropriate captions compared to the state of art models.
Human beings can describe scenarios and objects in a picture through vision easily, whereas performing the same task with a computer is a complicated one. Generating captions for the objects of an image helps everyone to understand the scenario of the image in a better way. Instinctively describing the content of an image requires the apprehension of computer vision as well as natural language processing. This task has gained huge popularity in the field of technology, and there is a lot of research work being carried out. Recent works have been successful in identifying objects in the image but are facing many challenges in generating captions to the given image accurately by understanding the scenario. To address this challenge, we propose a model to generate the caption for an image. Residual Neural Network (ResNet) is used to extract the features from an image. These features are converted into a vector of size 2048. The caption generation for the image is obtained with Long Short-Term Memory (LSTM). The proposed model was experimented with on the Flickr8K dataset and obtained an accuracy of 88.4%. The experimental results indicate that our model produces appropriate captions compared to the state of art models.
- Published in CSE NEWS, Departmental News, News, Research News
Boosting Transitive Communication in Large-scale IoT Networks

Complex IoT networks comprise multiple devices connected to the gateway. A smoother functioning is ensured through new techniques for device authentication to the gateway. On this note, the research paper titled “A Lightweight Mutual and Transitive Authentication Mechanism for IoT Network” has been published by Dr Amit Kumar Mandal, Assistant Professor, Department of Computer Science and Engineering and his research scholar Mrs Rudra Krishna Srija in the Q1 Journal Ad Hoc Networks, Elsevier having an impact factor of 4.8. The research details the use of the polynomial-based protocol in enhancing device connection for transitive communication.
Abstract of the paper
In large and complex IoT systems like the smart city or smart industry which consist of thousands of connected devices, it may not always be feasible to be directly connected to the gateway but it may be possible to be connected to another device. Therefore, already authenticated devices should facilitate the new device’s authentication by the gateway. To address this issue, the existing protocols use multiple authentication protocols based on different cryptography techniques, which are difficult to implement and manage in resource-constrained IoT devices. In this paper, we propose a Transitive device authentication protocol based on the Chebyshev polynomial.
The work is primarily aimed at improving transitive communication in machine-to-machine communication or device-to-device communication in large-scale heterogeneous IoT network scenarios. The research team targets to investigate the benefits of adopting the designed protocol in particular within low-power and lossy networks in the future.
Collaborations
Università Ca Foscari Venezia, Venice, Italy
- Published in CSE NEWS, Departmental News, News, Research News







