Ms M Krishna Kumari’s Innovative Approach to Adaptive NDN Caching
 Assistant Professor, Dr M Krishna Kumari, Assistant Professor, Department of Computer Science and Engineering, SRM University AP, has published her paper “Adaptive NDN Caching: Leveraging Dynamic Behaviour for Enhanced Efficiency” in the Q1 Journal of Network and Computer Applications with an impact factor of 8.0. The paper reimagines the internet using Named Data Networking
Assistant Professor, Dr M Krishna Kumari, Assistant Professor, Department of Computer Science and Engineering, SRM University AP, has published her paper “Adaptive NDN Caching: Leveraging Dynamic Behaviour for Enhanced Efficiency” in the Q1 Journal of Network and Computer Applications with an impact factor of 8.0. The paper reimagines the internet using Named Data Networking
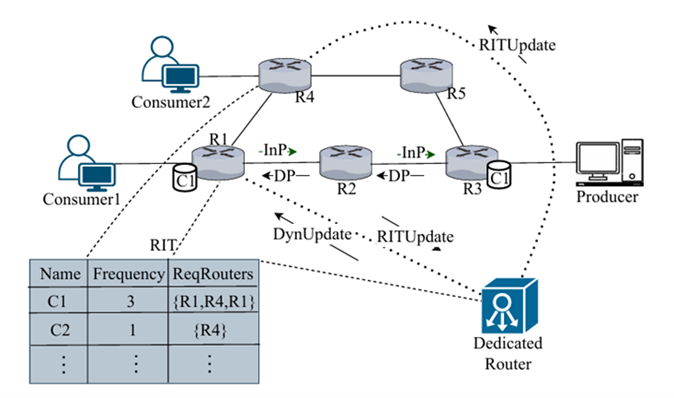
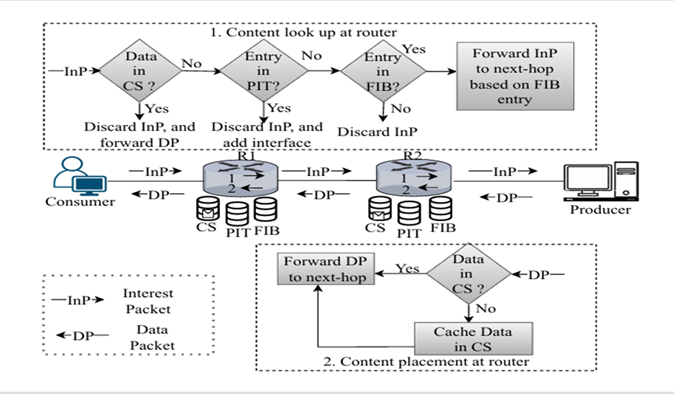
(NDN), which shifts the focus from location to data-centric communication. The study introduces an adaptive caching strategy that will lead to faster responses, smoother access, and fewer delays, even when tested on real-world topologies.
Abstract of the Research:
The publication “Adaptive NDN Caching: Leveraging Dynamic Behaviour for Enhanced Efficiency” proposes a dynamic caching strategy for Named Data Networking (NDN), a next- generation Internet architecture that shifts from host-based to data-centric communication. The approach continuously adapts to real-time content demand by monitoring request patterns and intelligently placing frequently accessed data closer to end users. This adaptive mechanism enhances efficiency, reduces delays, and improves overall network performance when tested on real-world topologies.
Layperson’s Explanation:
The Internet today focuses on where data comes from (IP addresses), but modern users care about what the data is. Applications such as video streaming, online education, AI, and IoT require data instantly, regardless of its source. NDN reimagines the Internet by focusing on data itself. The caching strategy ensures that routers learn which content is most frequently requested and bring it closer to the users. This means faster responses, smoother access, and less congestion, even during heavy network load.
Practical Implementation and Social Implications:Traditional TCP/IP struggles with scalability, congestion, and security. In contrast, NDN is a
future Internet architecture designed for delay-sensitive and data-driven environments. This is
vital because:
- In AI and IoT, even a fraction of delay can disrupt real-time processing.
- In VANETs (Connected Vehicular Networks), delays of milliseconds can mean serious
danger for safety-critical applications. - In tactical and mission-critical communications, reliability and speed can determine
mission success.
The caching innovation strengthens NDN’s role in delivering secure, delay-sensitive, and efficient communication for these emerging domains, while also reducing congestion and making networks more sustainable.
Collaborations:
This research is a collaboration between the Department of Computer Science and Engineering, SRM University-AP, Amaravati, and the Department of Computer Science and Engineering, Indian Institute of Technology (ISM, Dhanbad), in collaboration with Dr. Nikhil Tripathi (IIT Dhanbad).
Future Research Plans:
Future directions include extending adaptive caching to vehicular networks (VANETs), tactical communications, and other mission-critical systems, with a focus on AI-driven predictive caching for real-time applications. The goal is to enable networks to anticipate demand, ensure secure data delivery, and minimize delays, which
Photographs related to the research:
Transforming IoT Performance: Deep Learning in the Fog–Cloud Continuum

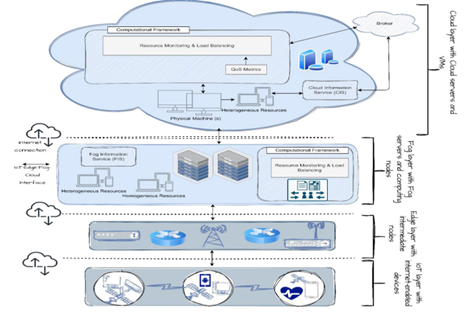
In the paper titled “Deep Learning-centric Task Offloading in IoT-Fog-Cloud Continuum: A State-of-the-Art Review, Open Research Issues and Future Directions,” by Dr Kshira Sagar Sahoo, Assistant Professor, Department of Computer Science and Engineering, and collaborators, the role of machine learning and deep learning in optimising IoT systems is comprehensively reviewed. Published in IEEE Access (2025), the study examines how intelligent task offloading and resource allocation across the fog–cloud continuum can address challenges of latency, bandwidth, and privacy. The article highlights key open issues and future directions, offering insights for developing faster, more reliable, and secure IoT applications in domains such as healthcare, smart cities, autonomous vehicles, and industrial IoT.
Abstract
The rapid growth of IoT and real-time applications has created massive volumes of data, which are traditionally processed in cloud-centric systems. This approach often suffers from high latency, bandwidth limitations, and privacy risks. Fog computing, by bringing computation closer to IoT devices, offers a promising solution. Our study provides a comprehensive review of task offloading and resource allocation in fog–cloud continuum, with a focus on machine learning and deep learning–based approaches.
Explanation in Layperson’s Terms
With billions of smart devices (like wearables, sensors, and cameras) generating data every second, sending everything to the cloud for processing can cause delays and strain the internet. Imagine if your smartwatch had to send your heartbeat data across the globe before alerting you of a health issue—that delay could be dangerous. Our research looks at how to use fog–cloud continuum, where nearby devices like routers or gateways help with computation instead of sending everything to the cloud.
Practical Implementation
Findings from this survey can help design smarter IoT systems where tasks are offloaded efficiently to nearby fog or edge devices, reducing latency and improving reliability. Key applications include:
- Healthcare monitoring (real-time alerts)
- Smart cities (traffic management, surveillance)
- Autonomous vehicles (low-latency decision-making)
- Industrial IoT (automation, predictive maintenance)
Social Impact
- Faster decision-making: Improves user safety and experience by cutting delays.
- Cost efficiency: Reduces operational costs by lowering dependence on cloud-only processing.
- Data privacy: Sensitive data can be processed closer to the source, enhancing security.
Collaborations
This research is a joint collaboration between:
- University of Saskatchewan, Saskatoon, SK, Canada
- GITAM Deemed to be University, Visakhapatnam, India
- SRM University-AP
Future Research Plans
- Developing lightweight, explainable AI models for task offloading on constrained IoT devices.
- Extending research into cybersecurity in IoT–Fog–Cloud systems, particularly DDoS detection and mitigation.
- Published in CSE NEWS, Departmental News, News, Research News
Dr Aswani on Blockchain-Based Self-Sovereign Identity Management
 The book chapter “A Novel Blockchain-Based Self-Sovereign Identity Management System for IoT Devices” is a transformative exploration within the book “Decentralized Identity Systems: Innovations and Challenges.” Authored by Dr Aswani Devi Aguru, Assistant Professor, Department of CSEand co-authored by Dr Suresh Babu Erukala NIT Warangal, this chapter delves into the critical intersection of blockchain technology and identity management, specifically tailored for the rapidly evolving Internet of Things (IoT) landscape.
The book chapter “A Novel Blockchain-Based Self-Sovereign Identity Management System for IoT Devices” is a transformative exploration within the book “Decentralized Identity Systems: Innovations and Challenges.” Authored by Dr Aswani Devi Aguru, Assistant Professor, Department of CSEand co-authored by Dr Suresh Babu Erukala NIT Warangal, this chapter delves into the critical intersection of blockchain technology and identity management, specifically tailored for the rapidly evolving Internet of Things (IoT) landscape.
Brief Introduction of the Book Chapter.
This book chapter presents a novel blockchain-based self-sovereign identity (SSI) management system that promotes global interoperability by generating decentralized, secure, and unique identifiers for edge devices worldwide. The proposed system leverages the power of permissioned Blockchain, specifically Hyperledger Indy, a distributed ledger technology (DLT) designed for creating and managing decentralized identities. The EdDSA-based key management and Plenum Byzantine Fault Tolerant (BFT)-based consensus algorithm introduce novelty and effectiveness in the proposed framework compared to state-of-the-art works on identity management. The performance of Hyperledger Indy Blockchain is tested on Hyperledger Caliper in terms of run time of operations and transaction throughput. We proclaim that our work is one of the earliest studies on Blockchain-based SSI management on Hyperledger Indy.
Significance of the Book Chapter
The author expresses strong enthusiasm for designing novel frameworks for IoT device authentication utilising ECC and AEAD primitives, in addition to developing identity management solutions based on SSI. The alignment of the book’s topics with current research highlights their significance in the progression of these critical areas.
Target Audience:
Very limited research has been carried out on SSI for IoT devices. Researchers will find the book chapter helpful in beginning their research on Blockchain-based decentralised identity management of IoT devices.
Co-authors or other Major Contributors
Dr Suresh Babu Erukala is a co-author. He is working as an Associate Professor in the Department of CSE at NIT Warangal.
The Link to the Book Chapter Publication
- Published in CSE NEWS, Departmental News, News, Research News
A Secure Framework for Embedding Secret Messages within Cover Images
 The Department of Computer Science and Engineering has filed and published a patent application titled “System and Method for Securely Concealing a Secret Message within a Cover Image” (Application No. 202541072940) in the Patent Office Journal. The invention is credited to Dr Subhankar Ghatak, Assistant Professor, Department of CSE, Dr Aurobindo Behera, Lecturer, Department of CSE (SRM Education), Ms Sharifa Jahan Shaik, U G Student, Department of CSE, and Ms Vasigani Jhansy Archana, Ph.D. Student, Department of CSE.
The Department of Computer Science and Engineering has filed and published a patent application titled “System and Method for Securely Concealing a Secret Message within a Cover Image” (Application No. 202541072940) in the Patent Office Journal. The invention is credited to Dr Subhankar Ghatak, Assistant Professor, Department of CSE, Dr Aurobindo Behera, Lecturer, Department of CSE (SRM Education), Ms Sharifa Jahan Shaik, U G Student, Department of CSE, and Ms Vasigani Jhansy Archana, Ph.D. Student, Department of CSE.
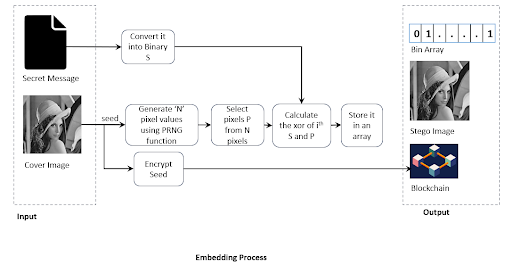
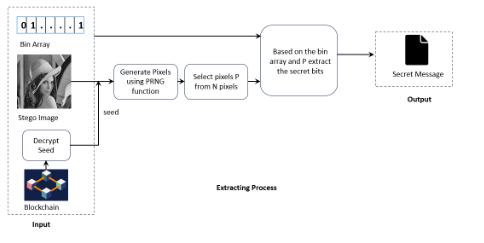
This innovation introduces a new paradigm in data hiding, advancing beyond conventional steganography techniques. Unlike traditional methods that subtly alter a cover image to embed secret information, this approach leaves the image entirely untouched.
By leveraging Pseudo-Random Number Generation (PRNG) in combination with the cover image and securely storing the PRNG seed value on the Blockchain, the system achieves unparalleled data security and integrity. As a result, the cover image remains completely unmodified, ensuring minimal distortion and highly reliable message retrieval.
Abstract :
This invention presents a novel approach to data hiding that differs from conventional steganography techniques. Unlike traditional methods, which modify the cover image to embed secret data, this methodology ensures the cover image remains completely unaltered. The technique employs Pseudo-Random Number Generation (PRNG) in conjunction with an array and the cover image to conceal secret data. The PRNG seed value is securely stored on the Blockchain, thereby enhancing both uniqueness and security. Since the cover image undergoes no modification, the proposed approach achieves a minimal Mean Squared Error (MSE) for the extracted secret image.
To hide a message in a picture, the usual way is to change the picture slightly—for example, by altering a few pixels so the difference is hard to notice. But if someone examines the image very closely, they might detect something unusual. Our method works differently. It’s like hiding a treasure without ever touching the map. Instead of altering it, we use a secret formula and a random number generator to decide where the hidden information would be if we needed to retrieve it later. The key to that formula is securely stored on the Blockchain, like locking it inside an unbreakable safe. As a result, the picture stays 100% original with no changes, and only the person who has the Blockchain secret key can uncover the hidden message.
Practical implementations :
Military Communication: Steganography can securely encode sensitive data, like that of meeting locations (latitude and longitude), ensuring that critical information remains hidden from adversaries.
Password Protection: Individuals can embed passwords within images, offering an additional layer of security and reducing the risk the unauthorized access.
Covert Communication: Activists or journalists in repressive regimes can use steganography to communicate securely by hiding messages within innocuous-looking images or files.
Medical Image Security: In healthcare, patient data can be securely embedded within medical images, ensuring data confidentiality while sharing the images with specialists.
Future research plans:
AI-Assisted Stealth Optimisation: Use Machine Learning to predict detection patterns and further improve the undetectability of hidden data.
Cross-Platform Media Support: Extend beyond images to videos, audio streams, and 3D models, ensuring zero modification across formats.
- Published in CSE NEWS, Departmental News, News, Research News
Patent on Feedback System for Faculty Insights
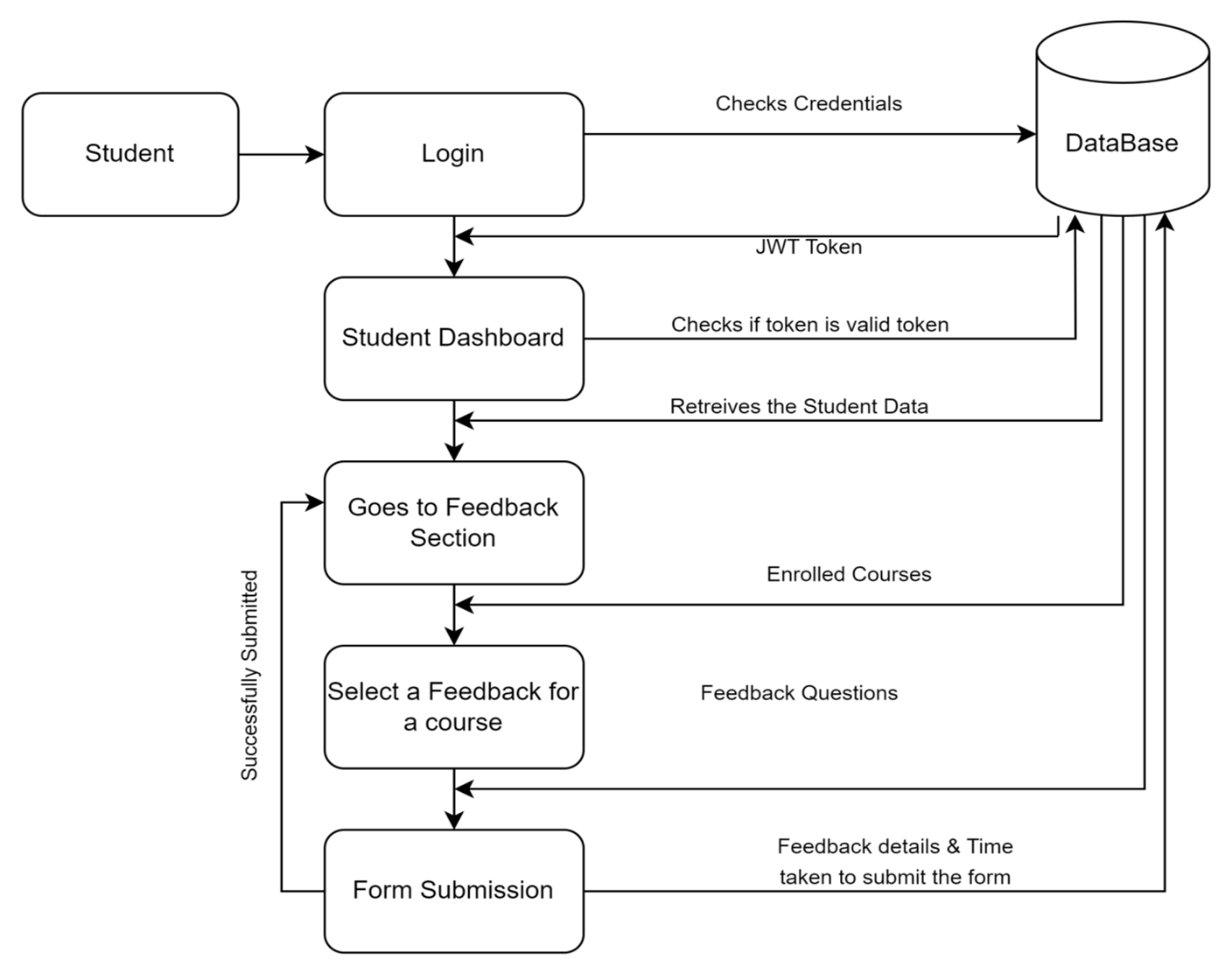
The faculties from the Department of Computer Scinece and Engineering, Dr Sasmita Rout, Dr Hema Kumar Yarnagula, and Dr Debabrata Senapati, along with their students and scholars, Mr Muthyala Sai Venkat, Mr Mukku Suhas, Mr Seelam Avinash Reddy, and Mr PV Manikanteswara Rao Baddi, introduce an innovative system that gathers student feedback on their learning experiences through questionnaires. By refining this feedback using specific metrics, the system delivers a more accurate assessment of faculty performance, ultimately enhancing teaching methods and creating a more engaging educational environment for students.
Brief Abstract of the Research
In the realm of higher education, student feedback is crucial and offers invaluable insights into the effectiveness of teaching methods. In addition, it helps faculty members by illuminating how their instructional practices affect student learning outcomes. The student feedback in academic settings empowers educators to adapt and refine their teaching strategies by identifying strengths and areas for improvement. Thus, ultimately creates a more engaging and impactful learning experience for the students. This article introduces a next-generation weighted student feedback system that collects responses using a set of questionnaires, referred to as the Conventional Feedback Score (CFS), from students about their learning experience and course effectiveness. The proposed system then refines the students’ responses based on three key metrics to provide a more accurate, balanced, and reliable assessment of the faculty performance. Our experimental results show that the proposed weighted feedback system provides a more accurate, reliable, and robust feedback score compared to CFS.
Explanation in Layperson’s Terms
The proposed feedback system is designed for use in academic settings such as colleges, universities, and online learning platforms seeking honest student evaluations. Any higher educational institution that prioritises quality teaching and fair assessments can benefit from the proposed system. Its key advantage lies in enhancing feedback reliability by minimising incorrect or irrelevant responses.
Practical Implementation and Social Implications associated with the Research
Any higher educational institution with an intent to prioritise quality teaching and fair assessments can benefit from the proposed system. Its key advantage lies in enhancing feedback reliability by minimising incorrect or irrelevant responses. This allows the institute administrators to make more informed decisions regarding faculty performance and instructional improvements. The system integrates easily with existing feedback mechanisms, enabling quick and efficient adoption. Primarily, this invention serves academic institutions aiming to collect accurate and fair student feedback for faculty evaluation.
Collaborations
In-house work with collaborations from IIT Guwahati and IIT Kharagpur
Future Research Plans
Plan to expanding the research and tackle challenges in areas such as real-time scheduling, embedded systems, and cyber-physical systems, with the aim of developing innovative solutions that address critical issues in these domains.
- Published in CSE NEWS, Departmental News, News, Research News
A Smart System for Optimised AAV Localization

By combining Particle Swarm Optimisation (PSO) and Fuzzy Logic, the team at SRM AP has discovered a hybrid smart system for accurate localization of autonomous aerial vehicles (AAVs). Dr Awadesh Dixit, Dr Firoj Gazi, Dr Muzakkir Hussain Md, Assistant Professors and MTech student Ms Naga Nandini Devi from the Department of Computer Science and Engineering, have published their research article “OALHMT: Optimised AAV Localization Using Hybrid Metaheuristic Techniques” in the IEEE Journal of Indoor and Seamless Positioning and Navigation, that discloses the making and implementation of this smart system that is precise and works better than current methods for positioning and navigation.
Abstract
Accurate localization remains a critical challenge for autonomous aerial vehicles (AAVs) due to their high-speed, multidirectional movement. Precise positioning is essential for efficient resource management and task reallocation during flight. This research proposes a bioinspired hybrid model combining Particle Swarm Optimization (PSO) with fuzzy logic to enhance AAV localization accuracy. PSO effectively explores the search space to identify optimal positions, while fuzzy logic fine-tunes the solution using real-time environmental inputs such as signal strength, sensor noise, and GPS inaccuracies. This synergistic approach leverages PSO’s global optimization with the contextual adaptability of fuzzy systems, delivering robust and precise localization under dynamic and noisy flight conditions. Comparative evaluations with existing methods demonstrate the model’s superior accuracy and responsiveness in real-time AAV operations.
Practical Implementation/Social Implication of the Research
Proposed hybrid optimization for Indoor localization through swarm UAVs, localization methods for autonomous aerial vehicles (AAVs) typically rely on the global positioning system (GPS), which is effective in open environments. GPS provides accurate real-time positional data, making it widely used for outdoor AAV localization.
The team will continue to focus on developing swarm-based V2X communication and coordination, and reduced interference, secure communication for enhance UAV networks performance, advance AI-related applications.
Link to the article
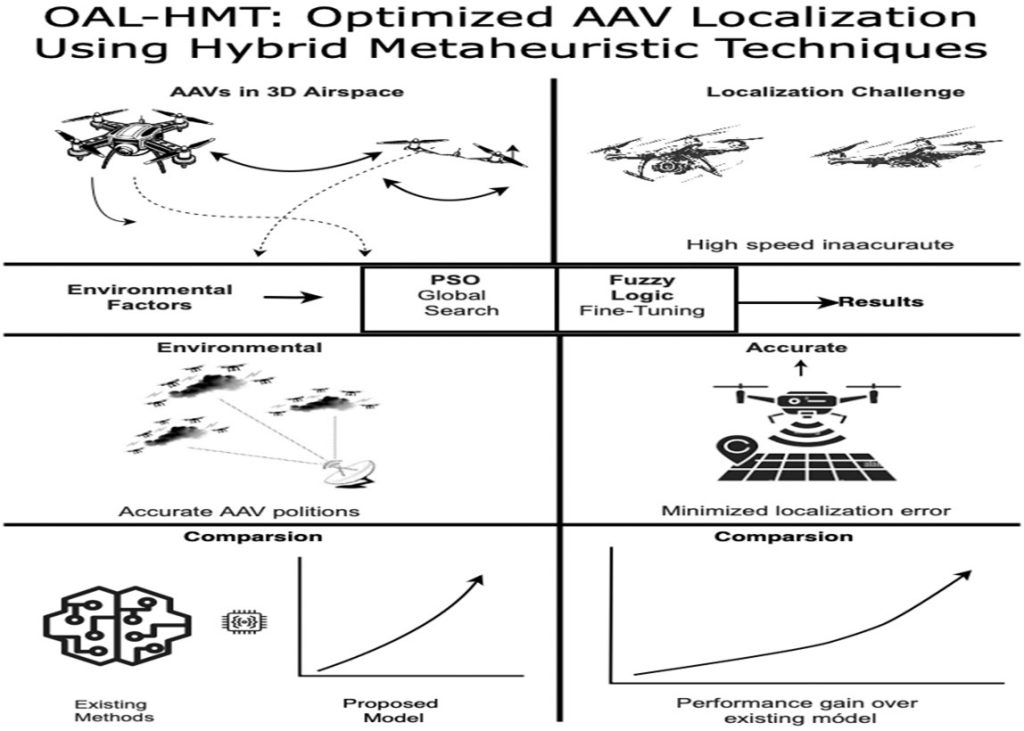
Overall abstract diagram of the paper
- Published in CSE NEWS, Departmental News, News, Research News
Team Ritorno Wins 1st Prize at ETHGlobal Cannes 2025, France
 We are immensely proud to celebrate the outstanding achievement of Team Ritorno—Satwik Batta and Shashank Chowdhary —B. Tech Computer Science, 4th Year Student from SRM University-AP, Amaravati, who have brought global recognition to Indian talent by securing 1st Prize at ETHGlobal Cannes 2025, hosted at Cannes University, France, from July 4–6, 2025.
We are immensely proud to celebrate the outstanding achievement of Team Ritorno—Satwik Batta and Shashank Chowdhary —B. Tech Computer Science, 4th Year Student from SRM University-AP, Amaravati, who have brought global recognition to Indian talent by securing 1st Prize at ETHGlobal Cannes 2025, hosted at Cannes University, France, from July 4–6, 2025.
Competing against over 350 teams and 1,500 participants from around the world, Team Ritorno emerged as winners at one of the most prestigious Ethereum hackathons, earning a cash prize of $4,500. Their winning project, “Topological Self-Healing Smart Contracts,” impressed a global jury and showcased their deep technical expertise and innovative spirit.
About ETHGlobal Cannes
ETHGlobal is a leading global platform for Ethereum hackathons, bringing together thousands of developers across six continents. The Cannes edition featured a prize pool of $275,000, supported by blockchain industry leaders like Polygon, Coinbase, Gnosis Chain, 1inch Network, and others.
Selection & University Support
Team Ritorno was selected for ETHGlobal Cannes after submitting their resumes and a compelling project proposal. Their idea, Topological Self-Healing Smart Contracts, was highly appreciated by the ETHGlobal organisers.
Before the event, the team presented their project to the Research Office and the Dean of SRM-AP, who were enthusiastic about their innovation and generously extended financial support of ₹2,10,000 to enable their participation.
“We’ve been working in this field since our second year. Our consistent participation gave us the exposure and confidence to compete globally,” the team shared. “The last week leading to ETHCannes was intense, and we are grateful to our university and faculty for their unwavering support.”
Looking Ahead
With eyes set on careers in top-tier U.S.-based tech companies, the trio is eager to continue pushing boundaries in blockchain and decentralised technologies.
Congratulations, Team Ritorno!
You’ve not only made SRM University-AP proud but have also put India’s innovation ecosystem on the global blockchain map. Your journey is an inspiration for all aspiring technologists.
- Published in CSE NEWS, Departmental News, News, Students Achievements
Dr Pradhan and Team’s Breakthrough in Post-Stroke Rehabilitation
 The Department of Computer Science and Engineering at SRM University-AP has yet again produced a scientific breakthrough. Associate Professor Dr Ashok Kumar Pradhan, along with his research scholars Mr Raheem Qudus and Ms Swetha Ghanta, published a patent on post-stroke rehabilitation using Virtual Reality and Artificial Intelligence.
The Department of Computer Science and Engineering at SRM University-AP has yet again produced a scientific breakthrough. Associate Professor Dr Ashok Kumar Pradhan, along with his research scholars Mr Raheem Qudus and Ms Swetha Ghanta, published a patent on post-stroke rehabilitation using Virtual Reality and Artificial Intelligence.
Brief Abstract of the Research
Stroke is one of the most significant health problems that aid disability and mortality in functionality of human health, While already there are varies approach, Traditionally and Technical methods developed to help patient overcome these challenges, common system to treat and help patients recovers from this are, using Local therapy approach, using EEG (electroencephalogram) and or using the BCI (Brain Computer Interface). However, not all patients find this approach applicable, suitable and affordable. The aim of this research is to perform Post-Stroke Rehabilitation recovery training and testing on patient without the need for Brain computer Interface (BCI) and Electroencephalogram (EEG), our proposed method provides similar embodiment and rehabilitation capabilities to those perceived from existing therapeutic techniques such as Constraint induced movement therapy (CIMT), Occupational therapy, mirror therapy and authenticating fear. Our Research approach resolution is to develop a virtual reality (VR) based system for post-stroke rehabilitation using Meta Quest (Headset) and Unity game engine for simulation of the virtual environment. Our emerging methods in integrating Generative-AI to provide adaptive therapy recommendations based on patient movements and engagement levels. While we implement the use of a real-time compensatory movement detection system without EEG, relying on AI-driven motion analysis.
Explanation in layperson’s terms:
After a stroke, patients often struggle to regain movement or perform simple tasks. Existing treatments rely on traditional and invasive signal equipment, such as wearing of electroencephalogram(EEG), and also require a professional expert to track and interpret the progress of the patient, while relying on real-world objects. Our invention solves those existing limitations through the integration of Virtual Reality (VR) and Artificial Intelligence (AI). We create a virtual world and object where stroke patients wear a VR headset and perform exercises in a simulated environment, while patients are able to feel a real-world immersive experience through movement practice, with a real-time communication guide of AI to aid users’ improvement.
Practical Implementation and Social Implications:
- Implementation: Clinics or homes can use our VR system to supplement therapy, reducing costs and therapist workload.
- Social Impact: Makes rehab accessible to low-income patients, avoids the stigma of bulky medical devices, and could reduce global stroke-related disability burdens.
- Accessible Therapy: Makes rehabilitation possible from home, especially in rural areas or underserved communities.
- Personalised Healing: The AI ensures therapy matches the patient’s ability in real time by providing real-time support during the session.
- Mental Health & Cognitive Benefit: Helps with memory, attention, and mood rehabilitation using immersive tasks.
Collaborations:
SRM University-AP, Amaravati (Assignee)
Future Research Plans:
- Expand the discovery into an adaptation framework for elderly care, PTSD treatment, and education for neurodivergent learners.
- Pilot clinical testing with actual stroke patients in collaboration with hospitals.
- Expand the system to support speech therapy and cognitive recovery tools.
- Integrating an AI-Agent for real-time Non-player character medical support during the immersive session.
- Published in CSE NEWS, Departmental News, News, Research News
Ensuring Food Safety through Artificial Intelligence
 Assistant Professor Dr Hemantha Kumar Kalluri from the Department of Computer Science and Engineering and post-doctoral fellow, Dr Premkumar Borugadda have published a research paper titled, A Comprehensive Analysis of Artificial Intelligence, Machine Learning, Deep Learning and Computer Vision in Food Science. This significant research explores how Artificial Intelligence (AI), Machine Learning (ML), Deep Learning (DL), and Computer Vision (CV) are making food processing smarter and more reliable.
Assistant Professor Dr Hemantha Kumar Kalluri from the Department of Computer Science and Engineering and post-doctoral fellow, Dr Premkumar Borugadda have published a research paper titled, A Comprehensive Analysis of Artificial Intelligence, Machine Learning, Deep Learning and Computer Vision in Food Science. This significant research explores how Artificial Intelligence (AI), Machine Learning (ML), Deep Learning (DL), and Computer Vision (CV) are making food processing smarter and more reliable.
Here’s a brief on their findings and the social and practical implementations of their work.
A Brief Abstract
Providing safe and quality food is crucial for every household and is of extreme significance in the growth of any society. It is a complex procedure that deals with all issues focusing on the development of food processing from seed to harvest, storage, preparation, and consumption. This current paper seeks to demystify the importance of Artificial Intelligence (AI), Machine Learning (ML), Deep Learning (DL), and Computer Vision (CV) in ensuring food safety and quality. By stressing the importance of these technologies, the audience will feel reassured and confident in their potential. These are very handy for such problems, giving assurance over food safety. CV is incredibly noble in today’s generation because it improves food processing quality and positively impacts firms and researchers. Thus, at the present production stage, rich in image processing and computer visioning is incorporated into all facets of food production. In this field, DL and ML are implemented to identify the type of food in addition to quality. Concerning data and result-oriented perceptions, one has found similarities regarding various approaches. As a result, the findings of this study will be helpful for scholars looking for a proper approach to identify the quality of food offered. It helps to indicate which food products have been discussed by other scholars and lets the reader know papers by other scholars inclined to research further. Also, deep learning is accurately integrated with identifying the quality and safety of foods in the market. This paper describes the current practices and concerns of ML, DL, and probable trends for its future development.
Explanation of the Research in Layperson’s Terms
The research explores how Artificial Intelligence (AI), Machine Learning (ML), Deep Learning (DL), and Computer Vision (CV) are making food processing smarter and more reliable.
AI and ML in Food Processing
- AI-powered systems can predict food spoilage, detect harmful contaminants, and ensure food is stored at the right temperature.
- ML models learn from past data to improve food quality, making processing more efficient and reducing waste.
Computer Vision (CV) for Food Inspection
- Cameras powered by AI can analyse food products and detect defects, ensuring only high-quality food reaches consumers.
- CV helps in sorting fruits and vegetables based on size, colour, and ripeness, reducing human error and speeding up production.
- It is also used to check food packaging for defects and prevent contamination.
Deep Learning for Better Food Safety
- Deep learning, a more advanced type of AI, helps identify patterns in food quality data.
- It is used to detect food adulteration (unwanted substances added to food), ensuring that the food we consume is pure and safe.
- DL models can also classify different types of food and analyse their nutritional content.
Future of Smart Food Processing
- As AI and ML continue to evolve, food production will become more automated, reducing human labour while increasing efficiency.
- These technologies will help minimise food waste, improve supply chains, and provide personalised nutrition recommendations.
- By integrating AI with real-time monitoring, food safety can be ensured on a global scale.
Practical Implementation and Social Implications
The research on Artificial Intelligence (AI), Machine Learning (ML), Deep Learning (DL), and Computer Vision (CV) in Food Science has significant real-world applications and social implications:
Practical Implementation
Our research has directed the researchers to develop applications in various stages of the food industry, from agriculture to food processing, quality control, and distribution. Here are some key practical implementations:
- Smart Food Inspection and Quality Control
1.1 Computer Vision (CV) & Deep Learning (DL) for Defect Detection
- AI-powered cameras can detect defects in fruits, vegetables, and packaged food (e.g., detecting bruises in apples and sorting out contaminated grains).
- AI enhances automated food grading and sorting, reducing human error.
1.2 AI for Food Adulteration Detection
- AI models analyse food samples for contaminants, chemical adulterants, and spoilage (e.g., identifying milk adulteration using spectral data).
- Deep learning algorithms predict shelf life based on packaging conditions.
2. AI in Food Safety and Hygiene Monitoring
2.1 AI-based Sensors for Real-time Food Safety Checks
- AI-driven sensors monitor temperature, humidity, and hygiene conditions in food storage units and supermarkets.
- ML-based forecasting predicts food spoilage before it happens, reducing foodborne diseases.
This research bridges the gap between technology and food security, ensuring that AI and ML can revolutionise the way food is produced, processed, and consumed. These technologies enhance quality control, reduce food waste, ensure hygiene, and support sustainable agriculture, leading to a healthier, safer, and more efficient global food system.
Future Research Plans.
AI-Powered Automated Food Sorting & Grading
- Use Computer Vision & Deep Learning to automate sorting of grains, fruits, and vegetables based on size, ripeness, and defects.
- Implement Deep Learning models for real-time sorting in food processing units.
- Published in CSE NEWS, Departmental News, News, Research News
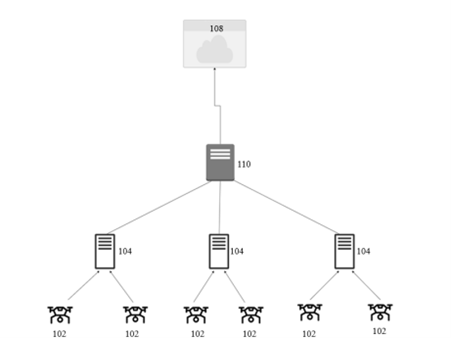
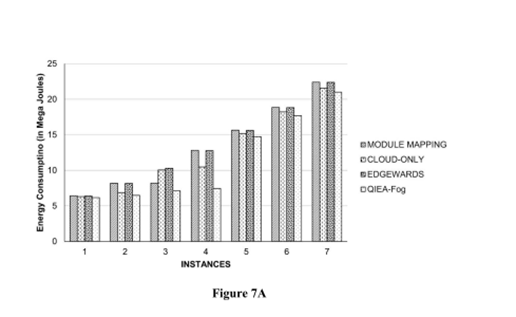
A Groundbreaking System for Fog-Based Animal Intrusion Detection
Dr Vemula Dinesh Reddy, Assistant Professor, Department of Computer Science and Engineering, has been granted a patent for his invention “A System And A Method for Fog-Based Animal Intrusion Detection” with the Application No: 202341026013, in the Indian Patent Official Journal. The invention acts as a groundbreaking fog computing-based system designed for real-time detection of animal intrusions in sensitive areas using smart sensors for instant alerts.
Abstract
This research introduces an intelligent system using fog computing to detect animal intrusions in sensitive or protected zones such as farmlands, highways, and forest borders. The system enables real-time data processing closer to the site of intrusion, offering faster detection and reduced dependency on centralised cloud systems. Furthermore, we proposed the Quantum-Inspired optimisation technique called Quantum Evolutionary Algorithm.
Practical Implementation/ Social Implications of the Research
Through this invention, we can:
- Prevent crop destruction and reduce human-wildlife conflict.
- Enhance safety on highways where animal crossings are common.
- Support forest conservation efforts by enabling non-intrusive monitoring.
- Reduce latency and bandwidth costs by processing data locally (via fog computing).
Future Research Plans
- Integrating AI-based species classification to identify specific animals.
- Creating a scalable mesh network for larger geographic coverage.
- Enhancing energy efficiency through solar-powered edge nodes.
- Extending the system to include drone-based visual surveillance.
- Published in CSE NEWS, Departmental News, News, Research News